- Research Article
- Open access
- Published:
Event Detection Using "Variable Module Graphs" for Home Care Applications
EURASIP Journal on Advances in Signal Processing volume 2007, Article number: 074243 (2007)
Abstract
Technology has reached new heights making sound and video capture devices ubiquitous and affordable. We propose a paradigm to exploit this technology for home care applications especially for surveillance and complex event detection. Complex vision tasks such as event detection in a surveillance video can be divided into subtasks such as human detection, tracking, recognition, and trajectory analysis. The video can be thought of as being composed of various features. These features can be roughly arranged in a hierarchy from low-level features to high-level features. Low-level features include edges and blobs, and high-level features include objects and events. Loosely, the low-level feature extraction is based on signal/image processing techniques, while the high-level feature extraction is based on machine learning techniques. Traditionally, vision systems extract features in a feed-forward manner on the hierarchy, that is, certain modules extract low-level features and other modules make use of these low-level features to extract high-level features. Along with others in the research community, we have worked on this design approach. In this paper, we elaborate on recently introduced V/M graph. We present our work on using this paradigm for developing applications for home care applications. Primary objective is surveillance of location for subject tracking as well as detecting irregular or anomalous behavior. This is done automatically with minimal human involvement, where the system has been trained to raise an alarm when anomalous behavior is detected.
References
Harrington C, Chapman S, Miller E, Miller N, Newcomer R: Trends in the supply of long-term-care facilities and beds in the United States. Journal of Applied Gerontology 2005,24(4):265-282. 10.1177/0733464805275366
Sethi A, Rahurkar M, Huang TS: Variable module graphs: a framework for inference and learning in modular vision systems. Proceedings of IEEE International Conference on Image Processing (ICIP '05), September 2005, Genova, Switzerland 2: 1326–1329.
Kschischang FR, Frey BJ, Loeliger H-A: Factor graphs and the sum-product algorithm. IEEE Transactions on Information Theory 2001,47(2):498-519. special issue on codes on graphs and iterative algorithms 10.1109/18.910572
Hinton GE: Products of experts. Proceedings of the 9th International Conference on Artificial Neural Networks (ICANN '99), September 1999, Edinburgh, UK 1: 1–6.
Neal RM, Hinton GE: A view of the EM algorithm that justifies incremental, sparse, and other variants. In Learning in Graphical Models. Edited by: Jordan MI. Kluwer Academic Publishers, Norwell, Mass, USA; 1999:355-368.
Dempster AP, Laird NM, Rubin DB:Maximum likelihood from incomplete data via the
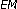 algorithm. Journal of the Royal Statistical Society. Series B 1977,39(1):1-38.
algorithm. Journal of the Royal Statistical Society. Series B 1977,39(1):1-38.McEliece RJ, MacKay DJC, Cheng J-F: Turbo decoding as an instance of Pearl's "belief propagation" algorithm. IEEE Journal on Selected Areas in Communications 1998,16(2):140-152. 10.1109/49.661103
Sethi A: Interaction between modules in learning systems for vision applications, Ph.D. thesis. University of Illinois at Urbana-Champaign, Champaign, Illinois, USA; 2006.
Frey BJ, Jojic N: A comparison of algorithms for inference and learning in probabilistic graphical models. IEEE Transactions on Pattern Analysis and Machine Intelligence 2005,27(9):1392-1416.
Sudderth EB, Ihler AT, Freeman WT, Willsky AS: Nonparametric belief propagation. Proceedings of the IEEE Computer Society Conference on Computer Vision and Pattern Recognition (CVPR '03), June 2003, Madison, Wis, USA 1: 605–612.
Heckerman D: A tutorial on learning with Bayesian networks. In Learning in Graphical Models. MIT Press, Cambridge, Mass, USA; 1999:301-354.
Margaritis D: Learning Bayesian network model structure from data, Ph.D. thesis. Department of Computer Science, Carnegie-Mellon University, Pittsburgh, Pa, USA; 2003.
Binder J, Koller D, Russell S, Kanazawa K: Adaptive probabilistic networks with hidden variables. Machine Learning 1997,29(2-3):213-244.
Bauer E, Koller D, Singer Y: Update rules for parameter estimation in Bayesian networks. Proceedings of the 13th Conference on Uncertainty in Artificial Intelligence (UAI '97), August 1997, Providence, RI, USA 3–13.
Gilks W, Richardson S, Spiegelhalter D: Markov Chain Monte Carlo in Practice. Chapman & Hall, London, UK; 1996.
Oliver NM, Rosario B, Pentland AP: A Bayesian computer vision system for modeling human interactions. IEEE Transactions on Pattern Analysis and Machine Intelligence 2000,22(8):831-843. 10.1109/34.868684
Li Y, Xu L-Q, Morphett J, Jacobs R: An integrated algorithm of incremental and robust PCA. Proceedings of International Conference on Image Processing (ICIP '03), September 2003, Barcelona, Spain 1: 245–248.
Lim J, Ross DA, Lin R-S, Yang M-H: Incremental learning for visual tracking. Advances in Neural Information Processing Systems (NIPS '04), December 2004, Vancouver, British Columbia, Canada
Johnson N, Hogg D: Learning the distribution of object trajectories for event recognition. Proceedings of the 6th British Conference on Machine Vision (BMVC '95), September 1995, Birmingham, UK 2: 583–592.
Kushal A, Rahurkar M, Li F-F, Ponce J, Huang TS: Audio-visual speaker localization using graphical models. Proceedings of the 18th International Conference on Pattern Recognition (ICPR '06), August 2006, Hong Kong 1: 291–294.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 2.0 International License (https://doi.org/creativecommons.org/licenses/by/2.0), which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
About this article
Cite this article
Sethi, A., Rahurkar, M. & Huang, T.S. Event Detection Using "Variable Module Graphs" for Home Care Applications. EURASIP J. Adv. Signal Process. 2007, 074243 (2007). https://doi.org/10.1155/2007/74243
Received:
Accepted:
Published:
DOI: https://doi.org/10.1155/2007/74243
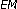 algorithm. Journal of the Royal Statistical Society. Series B 1977,39(1):1-38.
algorithm. Journal of the Royal Statistical Society. Series B 1977,39(1):1-38.