- Research Article
- Open access
- Published:
Dynamic Modeling of Internet Traffic for Intrusion Detection
EURASIP Journal on Advances in Signal Processing volume 2007, Article number: 090312 (2006)
Abstract
Computer network traffic is analyzed via mutual information techniques, implemented using linear and nonlinear canonical correlation analyses, with the specific objective of detecting UDP flooding attacks. NS simulation of HTTP, FTP, and CBR traffic shows that flooding attacks are accompanied by a change of mutual information, either at the link being flooded or at another upstream or downstream link. This observation appears to be topology independent, as the technique is demonstrated on the so-called parking-lot topology, random 50-node topology, and 100-node transit-stub topology. This technique is also employed to detect UDP flooding with low false alarm rate on a backbone link. These results indicate that a change in mutual information provides a useful detection criterion when no other signature of the attack is available.
References
Kent S: On the trail of intrusions into information systems. IEEE Spectrum 2000,37(12):52–56. 10.1109/6.887597
Moore D, Voelker G, Savage S: Inferring internet denial of service activity. Proceedings of the 10th USENIX Security Symposium, August 2001, Washington, DC, USA
Paxson V: Bro: a system for detecting network intruders in real-time. IEEE Computer Networks 1999,31(23–24):2435–2463. 10.1016/S1389-1286(99)00112-7
Roesch M: Snort-lightweight intrusion detection for networks. Proceedings of the USENIX LISA Conference on System Administration, November 1999, Seattle, Wash, USA 229–238.
Staniford S, Hoagland JA, McAlerney JM: Practical automated detection of stealthy portscans. Journal of Computer Security 2002,10(1–2):105–136.
Basseville M, Nikiforov I: Detection of Abrupt Changes: Theory and Application. Prentice Hall, Englewood Cliffs, NJ, USA; 1993.
Wang H, Zhang D, Shin KG: Change-point monitoring for the detection of DoS attacks. IEEE Transactions on Dependable and Secure Computing 2004,1(4):193–208. 10.1109/TDSC.2004.34
Siris VA, Papagalou F: Application of anomaly detection algorithms for detecting SYN flooding attacks. Proceedings of the IEEE Global Telecommunications Conference (GLOBECOM '04), November–December 2004, Dallas, Tex, USA 4: 2050–2054.
Wong C, Bielski S, McCune JM, Wang C: A study of mass-mailing worms. Proceedings of the ACM CCS Workshop on Rapid Malcode (WORM '04), October 2004, Washington, DC, USA
Whyte D, Kranakis E, van Oorschot PC: DNS-based detection of scanning worms in an enterprise network. Proceedings of the 12th Annual Network and Distributed System Security Symposium (NDSS '05), February 2005, San Diego, Calif, USA
Whyte D, Kranakis E, van Oorschot PC: ARP-based detection of scanning worms within an enterprise network. Proceedings of the 21st Annual Computer Security Applications Conference (ACSAC '05), December 2005, Tucson, Ariz, USA
Mirkovic J, Prier G, Reiher PL: Attacking DDoS at the source. Proceedings of the IEEE International Conference on Network Protocols (ICNP '02), November 2002, Paris, France 312–321.
Shah K, Bohacek S, Jonckheere E: On the predictability of data network traffic. Proceedings of the American Control Conference (ACC '03), June 2003, Denver, Colo, USA 2: 1619–1624.
Wallace CS, Dowe DL: Minimum message length and Kolmogorov complexity. The Computer Journal 1999,42(4):270–283. 10.1093/comjnl/42.4.270
Jonckheere E, Helton J: Power spectrum reduction by optimal hankel norm approximation of the phase of the outer spectral factor. IEEE Transactions on Automatic Control 1985,30(12):1192–1201. 10.1109/TAC.1985.1103864
Zvonkin A, Levin L: The complexity of finite objects and the development of the concepts of information and randomness by means of the theory of algorithms. Russian Mathematical Surveys 1970,25(6):83–124. 10.1070/RM1970v025n06ABEH001269
Sow DM, Eleftheriadis A: Complexity distortion theory. IEEE Transactions on Information Theory 2003,49(3):604–608. 10.1109/TIT.2002.808135
Manin YI: A Course in Mathematical Logic. Springer, New York, NY, USA; 1977.
Akaike H: Markovian representation of stochastic processes by canonical variables. SIAM Journal on Control 1975,13(1):162–173. 10.1137/0313010
Breiman L, Friedman JH: Estimating optimal transformations for multiple regression and correlation. Journal of the American Statistical Association 1985, 80: 580–619. 10.2307/2288473
Sipser M: Introduction to the Theory of Computation. PWS, Boston, Mass, USA; 1997.
Nemytskii VV, Stepanov VV: Qualitative Theory of Differential Equations. Dover, New York, NY, USA; 1989.
Brini F, Siboni S, Turchetti G, Vaienti S:Decay of correlations for the automorphism of the torus
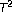 . Nonlinearity 1997,10(5):1257–1268. 10.1088/0951-7715/10/5/012
. Nonlinearity 1997,10(5):1257–1268. 10.1088/0951-7715/10/5/012Haydn N, Jonckheere EA: On mutual information. https://doi.org/eudoxus.usc.edu/CHAOS/traffic.html
Stallings W: High-Speed Networks TCP/IP and ATM Design Principles. 1st edition. Prentice Hall, Englewood Cliffs, NJ, USA; 1998.
Crovella ME, Bestavros A: Self-similarity in world wide web traffic: evidence and possible causes. IEEE/ACM Transactions on Networking 1997,5(6):835–846. 10.1109/90.650143
Feldmann A, Gilbert AC, Willinger W: Data networks as cascades: investigating the multifractal nature of Internet WAN traffic. Proceedings of the ACM Conference on Applications, Technologies, Architectures, and Protocols for Computer Communication (SIGCOMM '98), August–September 1998, Vancouver, BC, Canada 42–55.
Liu NX, Baras JS: On scaling property of network traffic in small scales. submitted to Computer Networks
Denning DE: An intrusion detection model. IEEE Transactions on Software Engineering 1987,13(2):222–232.
Ghosh A, Wanken J, Charron F: Detection anomalous and unknown intrusions agains programs. Proceedings of the 14th Annual Computer Security Applications Conference (ACSAC '98), Decemeber 1998, Scottsdale, Ariz, USA 259–267.
Javitz HS, Valdes A: The SRI IDES statistical anomaly detector. Proceedings of the IEEE Computer Society Symposium on Research in Security and Privacy, May 1991, Oakland, Calif, USA 316–326.
Ko C, Ruschitzka M, Levitt K: Execution monitoring of security-critical programs in distributed systems: a specification-based approach. Proceedings of the IEEE Computer Society Symposium on Research in Security and Privacy, May 1997, Oakland, Calif, USA 175–187.
Lane T, Brodley CE: Temporal sequence learning and data reduction for anomaly detection. Proceedings of the 5th ACM Conference on Computer and Communications Security (CCS '98), November 1998, San Francisco, Calif, USA 150–158.
Lee W, Stolfo S: A framework for constructing features and models for intrusion detection systems. Proceedings of the 5th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, August 1999, San Diego, Calif, USA
Forrest S, Hofmeyr SA, Somayaji A, Longstaff TA: A sense of self for unix processes. Proceedings of the IEEE Symposium on Security and Privacy, May 1996, Oakland, Calif, USA 120–128.
Anderson R, Khattak A: The use of information retrieval techniques for intrusion detection. Proceedings of the 1st International Workshop on the Recent Advances in Intrusion Detection (RAID '98), September 1998, Louvain-la-Neuve, Belgium
Teng HS, Chen K, Lu SC-Y: Adaptive real-time anomaly detection using inductively generated sequential patterns. Proceedings of the IEEE Computer Society Symposium on Research in Security and Privacy, May 1990, Oakland, Calif, USA 278–284.
Lunt T, Tamaru A, Gilham F, et al.: A real-time intrusion detection expert system (IDES). Computer Science Laboratory, SRI International, Menlo Park, Calif, USA; 1992.
Blazek RB, Kim H, Rozovskii B, Tartakovsky A: A novel approach to detection of denial-of service attacks via adaptive sequential and batch sequential change-point detection methods. Proceedings of the 2nd Annual IEEE Systems, Man, and Cybernetics Information Assurance Workshop, June 2001, New York, NY, USA
Wang H, Zhang D, Shin K: Detecting SYN flooding attacks. Proceedings of the 21st Annual Joint Conference of the IEEE Computer and Communications Societies (INFOCOM '02), June 2002, New York, NY, USA 3: 1530–1539.
Alarcon-Aquino V, Barria JA: Anomaly detection in communication networks using wavelets. IEE Proceedings: Communications 2001,148(6):355–362. 10.1049/ip-com:20010659
Thottan M, Ji C: Anomaly detection in IP networks. IEEE Transactions on Signal Processing 2003,51(8):2191–2204. 10.1109/TSP.2003.814797
Barford P, Kline J, Plonka D, Ron A: A signal analysis of network traffic anomalies. Proceedings of the 2nd ACM SIGCOMM Internet Measurement Workshop (IMW '02), November 2002, Marseille, France 71–82.
Cheng C-M, Kung HT, Tan K-S: Use of spectral analysis in defense against DoS attacks. Proceedings of the IEEE Global Telecommunications Conference (GLOBECOM '02), November 2002, Taipei, Taiwan 3: 2143–2148.
Hussain A, Heidemann J, Papadopoulos C: A framework for classifying denial of service attacks. Proceedings of the ACM Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications (SIGCOMM '03), August 2003, Karlsruhe, Germany 99–110.
Partridge C, Cousins D, Jackson A, Krishnan R, Saxena T, Strayer WT: Using signal processing to analyze wireless data traffic. Proceedings of the ACM Workshop on Wireless Security, September 2002, Atlanta, Ga, USA
Zhang Z-L, Ribeiro V, Moon S, Diot C: Small-time scaling behaviors of Internet backbone traffic: an empirical study. Proceedings of the 22nd Annual Joint Conference of the IEEE Computer and Communications Societies (INFOCOM '03), March–April 2003, San Francisco, Calif, USA 3: 1826–1836.
Evans S, Bush SF, Hershey J: Information assurance through Kolmogorov complexity. Proceedings of the 2nd DARPA Information Survivability Conference and Exposition II (DISCEX-II '01), June 2001, Anaheim, Calif, USA
Samoradnitsky G, Taqqu MS: Stable Non-Gaussian Random Processes, Stochastic Models with Infinite Variance. Chapman & Hall, New York, NY, USA; 1994.
Jonckheere E, Wu B-F: Mutual Kolmogorov-Sinai entropy approach to nonlinear estimation. Proceedings of the IEEE Conference on Decision and Control, December 1992, Tucson, Ariz, USA 2226–2232.
Kullback S: Information Theory and Statistics. Dover, New York, NY, USA; 1968.
Wu BF: Identification and control of chaotic processes—the Kolmogorov-Sinai entropy approach, Ph.D. dissertation.
Larimore WE: Identification and filtering of nonlinear systems using canonical variate analysis. In Nonlinear Modeling and Forecasting, SFI Studies in the Sciences of Complexity. Volume 12. Addison-Wesley, Reading, Mass, USA; 1991:283–303.
Leland W, Taqqu M, Willinger W, Wilson D: On the self-similar nature of Ethernet traffic (extended version). IEEE/ACM Transactions on Networking 1994,2(1):1–15. 10.1109/90.282603
Pruthi P, Erramilli A: Heavy-tailed ON/OFF source behavior and self-similar traffic. IEEE International Conference on Communications, June 1995, Seattle, Wash, USA 1: 445–450.
CERT : CERT advisory CA-96.01: UDP port denial-of-service attack. https://doi.org/info.cert.org/pub/cert_advisories/ca-96.01.udp_service_denial
ERT Coordination Center : Overview of attack trends. https://doi.org/www.cert.org/archive/pdf/attacktrends.pdf
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 2.0 International License ( https://creativecommons.org/licenses/by/2.0 ), which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
About this article
Cite this article
Shah, K., Jonckheere, E. & Bohacek, S. Dynamic Modeling of Internet Traffic for Intrusion Detection. EURASIP J. Adv. Signal Process. 2007, 090312 (2006). https://doi.org/10.1155/2007/90312
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1155/2007/90312
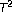 . Nonlinearity 1997,10(5):1257–1268. 10.1088/0951-7715/10/5/012
. Nonlinearity 1997,10(5):1257–1268. 10.1088/0951-7715/10/5/012