- Research Article
- Open access
- Published:
Secure Hashing of Dynamic Hand Signatures Using Wavelet-Fourier Compression with BioPhasor Mixing and 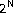 Discretization
Discretization
EURASIP Journal on Advances in Signal Processing volume 2007, Article number: 059125 (2006)
Abstract
We introduce a novel method for secure computation of biometric hash on dynamic hand signatures using BioPhasor mixing and discretization. The use of BioPhasor as the mixing process provides a one-way transformation that precludes exact recovery of the biometric vector from compromised hashes and stolen tokens. In addition, our user-specific
discretization. The use of BioPhasor as the mixing process provides a one-way transformation that precludes exact recovery of the biometric vector from compromised hashes and stolen tokens. In addition, our user-specific discretization acts both as an error correction step as well as a real-to-binary space converter. We also propose a new method of extracting compressed representation of dynamic hand signatures using discrete wavelet transform (DWT) and discrete fourier transform (DFT). Without the conventional use of dynamic time warping, the proposed method avoids storage of user's hand signature template. This is an important consideration for protecting the privacy of the biometric owner. Our results show that the proposed method could produce stable and distinguishable bit strings with equal error rates (EERs) of
discretization acts both as an error correction step as well as a real-to-binary space converter. We also propose a new method of extracting compressed representation of dynamic hand signatures using discrete wavelet transform (DWT) and discrete fourier transform (DFT). Without the conventional use of dynamic time warping, the proposed method avoids storage of user's hand signature template. This is an important consideration for protecting the privacy of the biometric owner. Our results show that the proposed method could produce stable and distinguishable bit strings with equal error rates (EERs) of and
and for random and skilled forgeries for stolen token (worst case) scenario, and
for random and skilled forgeries for stolen token (worst case) scenario, and for both forgeries in the genuine token (optimal) scenario.
for both forgeries in the genuine token (optimal) scenario.
References
Vielhauer C, Steinmetz R, Mayerhorf A: Biometric hash based on statistical features of online signatures. Proceedings of 16th International Conference on Pattern Recognition (ICPR '02), August 2002, Quebec, Canada 1: 123–126.
Vielhauer C, Steinmetz R: Handwriting: feature correlation analysis for biometric hashes. EURASIP Journal on Applied Signal Processing 2004,2004(4):542–558. special issue on Biometric Signal Processing 10.1155/S1110865704309248
Feng H, Chan CW: Private key generation from on-line handwritten signatures. Information Management & Computer Security 2002,10(4):159–164. 10.1108/09685220210436949
Chang Y-J, Zhang W, Chen T: Biometrics-based cryptographic key generation. Proceedings of the IEEE International Conference on Multimedia and Expo (ICME '04), June 2004, Taipei, Taiwan 3: 2203–2206.
Soutar C, Roberge D, Stoianov A, Gilroy R, Kumar BV: Biometric encryption using image processing. Optical Security and Counterfeit Deterrence Techniques II, January 1998, San Jose, Calif, USA, Proceedings of SPIE 3314: 178–188.
Juels A, Wattenberg M: A fuzzy commitment scheme. In Proceedings of the 6th ACM Conference on Computer and Communications Security (CCS '99), November 1999, Singapore Edited by: Tsudik G. 28–36.
Juels A, Sudan M: A fuzzy vault scheme. In Proceedings of IEEE International Symposium on Information Theory (ISIT '02), June–July 2002, Lausanne, Switzerland Edited by: Lapidoth A, Teletar E. 408.
Clancy TC, Kiyavash N, Lin DJ: Secure smartcard-based fingerprint authentication. Proceedings of the ACM SIGMM Workshop on Multimedia Biometrics Methods and Applications (WBMA '03), November 2003, Berkley, Calif, USA 45–52.
Goh A, Ngo D-CL: Computation of cryptographic keys from face biometrics. Proceedings of 7th IFIP International Conference on Communications and Multimedia Security (CMS '03), October 2003, Torino, Italy, Lecture Notes in Computer Science 2828: 1–13.
Yip W-K, Goh A, Ngo D-CL, Teoh A-BJ: Generation of replaceable cryptographic keys from dynamic handwritten signatures. Proceedings of International Conference on Advances in Biometrics (ICB '06), 2006, Hong Kong, Lecture Notes in Computer Science 3832: 509–515.
Yip W-K, Goh A, Ngo D-CL, Teoh A-BJ: Cryptographic keys from dynamic hand-signatures with biometric secrecy preservation and replaceability. Proceedings of the 4th IEEE on Automatic Identification Advanced Technologies (AutoID '05), October 2005, Buffalo, NY, USA 27–32.
Liu K, Kargupta H, Ryan J: Random projection-based multiplicative data perturbation for privacy preserving distributed data mining. IEEE Transactions on Knowledge and Data Engineering 2006,18(1):92–106.
Kholmatov A, Yanikoglu B: Biometric authentication using online signatures. Proceedings of the 19th International Symposium on Computer and Information Sciences (ISCIS '04), October 2004, Kemer-Antalya, Turkey, Lecture Notes in Computer Science 3280: 373–380.
Feng H, Chan CW: Online signature verification using a new extreme points warping technique. Pattern Recognition Letters 2003,24(16):2943–2951. 10.1016/S0167-8655(03)00155-7
Martinez JCR, Lopez JJV, Rosas FJL: A low-cost system for signature recognition. Proceedings of International Congress on Research in Electrical and Electronics Engineering (ELECTRO '02), 2002
Hastie T, Kishon E, Clark M, Fan J: A model for signature verification. Proceedings of IEEE International Conference on Systems, Man, and Cybernetics, October 1991, Charlottesville, VA, USA 1: 191–196.
Vergara da Silva A, Santana de Freitas D: Wavelet-based compared to function-based on-line signature verification. Proceedings of the 15th Brazilian Symposium on Computer Diagramics and Image Processing (SIBGRAPI '02), October 2002, Fortaleza-CE, Brazil 218–225.
Deng PS, Liao H-YM, Ho CW, Tyan H-R: Wavelet-based off-line handwritten signature verification. Computer Vision and Image Understanding 1999,76(3):173–190. 10.1006/cviu.1999.0799
Lejtman DZ, George SE: On-line handwritten signature verification using wavelets and back-propagation neural networks. Proceedings of 6th International Conference on Document Analysis and Recognition (ICDAR '01), September 2001, Seattle, Wash, USA 992–996.
Nakanishi I, Nishiguchi N, Itoh Y, Fukui Y: On-line signature verification method utilizing feature extraction based on DWT. Proceedings of IEEE International Symposium on Circuits and Systems (ISCAS '03), May 2003, Bangkok, Thailand 4: IV-73–IV-76.
Lam CF, Kamins D: Signature recognition through spectral analysis. Pattern Recognition 1989,22(1):39–44. 10.1016/0031-3203(89)90036-8
SVC First International Signature Verification Competition, 2004, https://doi.org/www.cs.ust.hk/svc2004/
Teoh A-BJ, Ngo D-CL: Cancellable biometrics realization through biophasoring. Proceedings of 9th IEEE International Conference on Control, Automation, Robotics and Vision (ICARCV '06), December 2006, Singapore
Cover TM, Thomas JA: Elements of Information Theory. 2nd edition. John Wiley & Sons, New York, NY, USA; 1991.
Shannon CE: Communication Theory of Secrecy Systems. Bell Systems Technical Journal 1949, 28: 656–715.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 2.0 International License (https://doi.org/creativecommons.org/licenses/by/2.0), which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
About this article
Cite this article
Wai Kuan, Y., Teoh, A.B.J. & Ngo, D.C.L. Secure Hashing of Dynamic Hand Signatures Using Wavelet-Fourier Compression with BioPhasor Mixing and 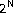 Discretization.
EURASIP J. Adv. Signal Process. 2007, 059125 (2006). https://doi.org/10.1155/2007/59125
Discretization.
EURASIP J. Adv. Signal Process. 2007, 059125 (2006). https://doi.org/10.1155/2007/59125
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1155/2007/59125